CNS Summer 2023 Previous Year Paper Solutions
Q1
(a) List and define the three security goals.
- Confidentiality: This ensures that information is accessible only to those who are authorized to access it. It involves protecting data from unauthorized access or disclosure.
- Integrity: Integrity ensures that information is accurate, consistent, and trustworthy. It involves protecting data from unauthorized modification or tampering.
- Availability: Availability ensures that information and resources are accessible and usable when needed by authorized users. It involves ensuring that systems are reliable and resilient against attacks or failures that could disrupt access to resources.
(b) Distinguish between passive and active security attacks
| Active attack | Passive attack |
|---|---|
| In active attack, actual message gets changed by attacker. | In passive attack, actual message is observed by attacker. |
| Active attack is easy to detect | It is harder to detect |
| They can break confidentiality, integrity, and availability of data or systems. | They may break the confidentiality of data. |
| Examples - malware, denial-of-service (DoS) attacks, man-in-the-middle (MITM) attacks. | Examples - eavesdropping, traffic analysis, and cryptanalysis. |
| Types - Masquerade, message modification, replay, DOS | Types - Release of content, Traffic analysis |
(c) Define Cryptography and Cryptanalysis. Draw and explain conventional cryptosystem.
Cryptography:
Cryptography is the practice and study of techniques for securing communication and data by converting plain text into cipher text using key and encryption algorithm and also converting the cipher text back to plain text.
Cryptanalysis:
Cryptanalysis is the study of analyzing and deciphering encrypted information without having access to the secret key or algorithm used to encrypt it. It involves various techniques such as frequency analysis, brute force attacks, and exploiting vulnerabilities in encryption algorithms to recover the plaintext from ciphertext.
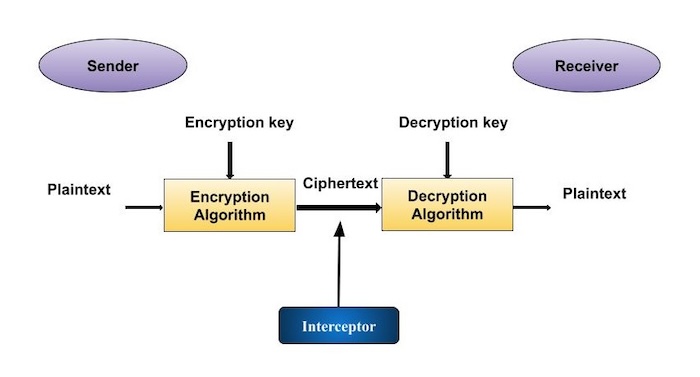
Terminology:
- Plaintext: It is the actual message
- Key: A secret parameter used in encryption and decryption algorithms to control the transformation of plaintext into ciphertext and vice versa.
- Encryption: The process of converting plaintext into ciphertext using an encryption algorithm and a key.
- Ciphertext: The encrypted, unintelligible form of data resulting from the encryption process.
- Decryption: The process of converting ciphertext back into plaintext using a decryption algorithm and the appropriate key.
Procedure:
- When sender wants to send message to receiver, they will encrypt message using encryption key
- Now message is unreadable or unintelligible form, so attacker can’t read it.
- At receiver side, receiver gets cipher text
- Receiver decrypts cipher text using same key by which it was converted from plaintext to cipher text, and then gets the actual message.
Q2
(a)Define (i) group (ii) Ring (iii) Field
(i) group:
A mathematical set along with a binary operation that satisfies closure, associativity, identity element, and inverse element properties.
(ii) ring:
A mathematical structure consisting of a set equipped with two binary operations, addition and multiplication, that satisfy closure, associativity, distributivity, and the presence of an additive identity element.
(iii) Field:
It is defined as arbitrary ring which satisfies below property:
- Multiplicative inverse: If multiplicative inverse of element a is also in the group, then it satisfies the property.
(b) Distinguish between
(i) substitution cipher and transposition cipher
| Aspect | Substitution Cipher | Transposition Cipher |
|---|---|---|
| Operation | It substitutes each plaintext character or group of characters with a different character or group of characters. | It rearranges the order of characters in the plaintext without altering them. |
| Complexity | Generally simpler in concept and implementation. | Generally more complex in concept and implementation. |
| Example | Caesar cipher, Atbash cipher, Affine cipher. | Rail Fence cipher, Columnar Transposition cipher. |
(ii) monoalphabetic cipher and polyalphabetic cipher
| Aspect | Monoalphabetic Cipher | Polyalphabetic Cipher |
|---|---|---|
| Key Usage | Utilizes a single fixed substitution alphabet for the entire encryption process. | Employs multiple substitution alphabets, frequently changing during the encryption process. |
| Complexity | Simpler in concept and implementation compared to polyalphabetic ciphers. | More complex due to the need for multiple substitution alphabets and key management. |
| Security Strength | Generally less secure, susceptible to frequency analysis and other attacks. | Offers better security compared to monoalphabetic ciphers, as the use of multiple alphabets complicates cryptanalysis. |
| Examples | Caesar cipher, Atbash cipher, Simple Substitution cipher. | Vigenère cipher, Playfair cipher, Autokey cipher. |
(c) Discuss ECB & CBC block cipher modes of operation with the help of
diagram
Electronic Codebook (ECB):
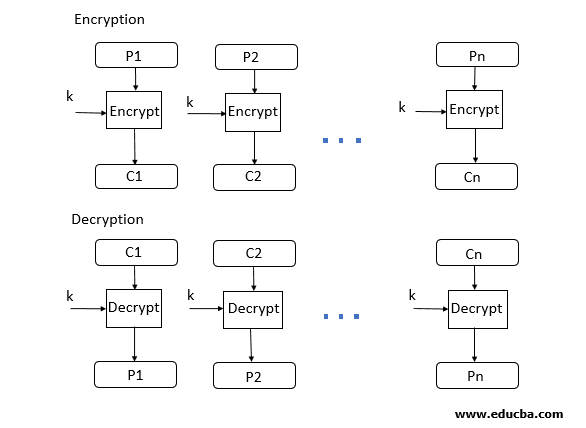
- In ECB mode, each block of plaintext is encrypted separately with the same key. This means that identical plaintext blocks will produce identical ciphertext blocks.
- The plaintext is divided into fixed-size blocks, typically 64 or 128 bits, and each block is encrypted independently using the encryption algorithm and the shared key.
- Advantages:
- Simplicity: ECB mode is straightforward to implement and parallelize, making it efficient for hardware implementations.
- Disadvantages:
- Lack of diffusion: Identical plaintext blocks produce identical ciphertext blocks, which can leak information about the structure of the plaintext.
- Vulnerable to pattern analysis: Patterns in the plaintext can be discerned from patterns in the ciphertext, which may compromise security.
Cipher Block Chaining (CBC):
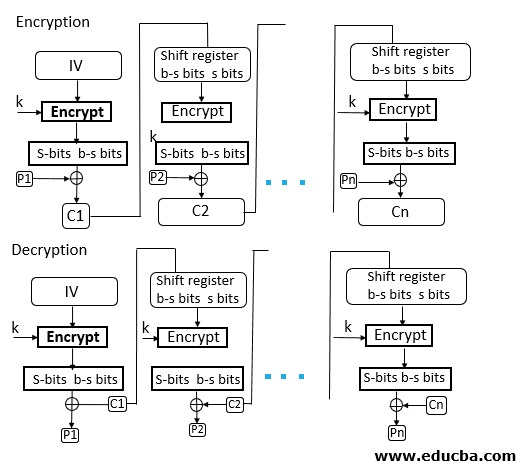
In CBC mode, each plaintext block is XORed with the ciphertext of the previous block before encryption. This introduces feedback into the encryption process, making each ciphertext block dependent on all preceding plaintext blocks.
CBC mode requires an initialization vector (IV) to be XORed with the first plaintext block. Subsequent plaintext blocks are XORed with the ciphertext of the previous block before encryption.
- Advantages:
- Diffusion: CBC mode propagates changes in the plaintext throughout the ciphertext, making it resistant to pattern analysis.
- Randomization: The IV introduces randomness into the encryption process, ensuring that identical plaintext blocks encrypted with the same key produce different ciphertext blocks.
- Disadvantages:
- Sequential processing: CBC mode requires sequential processing of blocks, making it less suitable for parallel implementations compared to ECB mode.
- Padding requirements: CBC mode may require padding of the plaintext to ensure that it can be divided into complete blocks.
OR
(c) Discuss Cipher Feedback & Output Feedback block cipher modes of operation with the help of a diagram

- In CFB mode, the encryption algorithm is applied to the previous ciphertext block to generate a pseudorandom output, which is then XORed with the current plaintext block to produce the ciphertext.
- CFB mode operates on blocks of plaintext, similar to CBC mode. However, instead of XORing the plaintext with the previous ciphertext block directly, CFB mode generates a pseudorandom output using the encryption algorithm and the previous ciphertext block. This output is then XORed with the plaintext to produce the ciphertext.
- Advantages:
- Error propagation: CFB mode propagates errors in the ciphertext, preventing them from affecting subsequent plaintext blocks.
- Bit-level encryption: CFB mode allows for encryption and decryption at the bit level, which can be useful in certain applications.
- Disadvantages:
- Error recovery: CFB mode requires error recovery mechanisms to synchronize the encryption and decryption processes in the event of errors or data loss.
- Overhead: CFB mode introduces additional computational overhead due to the need for bit-level encryption and error recovery mechanisms.
Output Feedback (OFB):
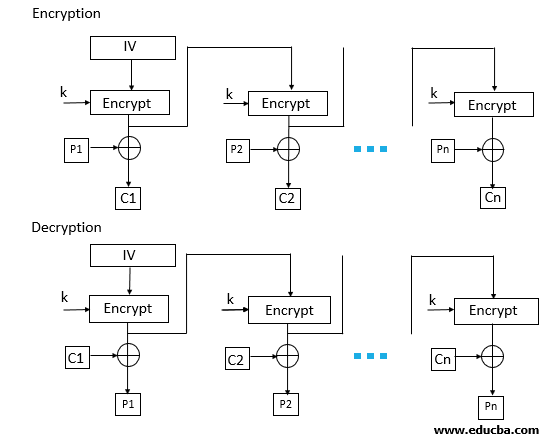
- In OFB mode, the encryption algorithm is applied to an initial value (IV) to generate a keystream, which is then XORed with the plaintext to produce the ciphertext.
- OFB mode operates similarly to CFB mode but generates a keystream independently of the plaintext. The IV is encrypted to produce the first keystream, which is then XORed with the plaintext to produce the ciphertext. Subsequent keystreams are generated by encrypting the previous keystream.
- Advantages:
- Error propagation: OFB mode propagates errors in the ciphertext, preventing them from affecting subsequent plaintext blocks.
- Independence: OFB mode allows for parallel encryption and decryption processes, as the keystream can be generated independently of the plaintext.
- Disadvantages:
- Synchronization: OFB mode requires synchronization between the encryption and decryption processes to ensure that the same keystream is used.
- Lack of diffusion: Unlike CBC mode, OFB mode does not propagate changes in the plaintext throughout the ciphertext, potentially leading to security vulnerabilities.
Q3
(a) Encrypt the Message “BALLOON” with key using Hill Cipher.
Message = “BALLOON”
Key =
Hill Cipher = kp mod 26
- Encrypting BA:
= mod 26 = =
- Encrypting LL:
= mod 26 = =
- Encrypting OO:
= mod 26 = =
- We’ll fill the last letter by X
∴ =
Cipher text - DFDCSMHS
(b) Find GCD of 1970 and 1066 using Euclid algorithm
To find the greatest common divisor (GCD) of 1970 and 1066 using the Euclidean algorithm, we iteratively apply the algorithm until we reach a remainder of 0.
| Q | A | B | R |
|---|---|---|---|
| 1 | 1970 | 1066 | 904 |
| 1 | 1066 | 904 | 162 |
| 5 | 904 | 162 | 94 |
| 1 | 162 | 94 | 68 |
| 1 | 94 | 68 | 26 |
| 2 | 68 | 26 | 16 |
| 1 | 26 | 16 | 10 |
| 1 | 16 | 10 | 6 |
| 1 | 10 | 6 | 4 |
| 1 | 6 | 4 | 2 |
| 2 | 4 | 2 | 0 |
| 2 | 0 |
1970 = 1066 * 1 + 904
1066 = 904 * 1 + 162
904 = 162 * 5 + 94
162 = 94 * 1 + 68
94 = 68 * 1 + 26
68 = 26 * 2 + 16
26 = 16 * 1 + 10
16 = 10 * 1 + 6
10 = 6 * 1 + 4
6 = 4 * 1 + 2
4 = 2 * 2 + 0
gcd(1970, 1066) = 2
(c) Explain single round function of DES with suitable diagram
The Data Encryption Standard (DES) is a symmetric-key block cipher that operates on blocks of plaintext and ciphertext of 64 bits each. In DES, a single round of the algorithm consists of several operations, including permutation, substitution, and key mixing. It converts plaintext to cipher text in 16 rounds.
Explanation:
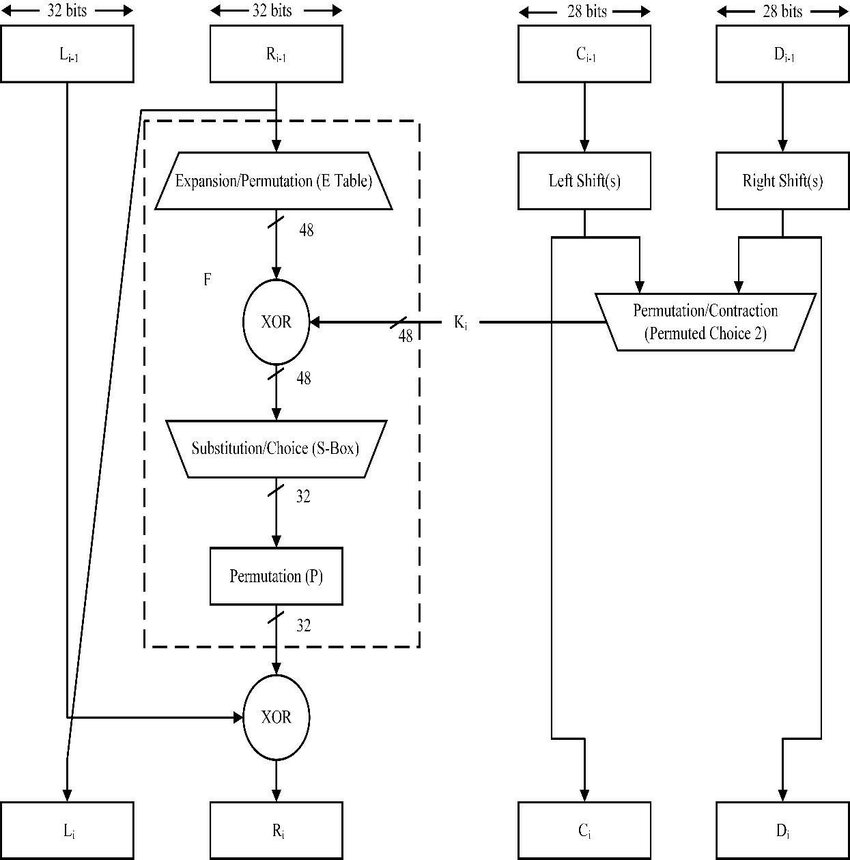
- The 64 bit plain text is divided into two equal halves (32 bit each)
- Since the key is of 48 bits, we use expansion permutation to increase 32 bits to 48 bits (by adding 16 bits)
- Then perform XOR, of this 48 bits and 48 bits key
- Now use S-box to again reduce 16 bits. There are 8 S-boxes
- Each S-box takes 6 bits and outputs 4 bits
How S-box works
- Since it takes 6 bits, the first and last bits determine the row and the middle 4 bits determine the column
- We have a pre-defined table in which we take the value present at that location and represent that value in 4 bits in binary
After 16 rounds of encryption, final cipher text will be generated.
OR
Q3
Q4
(a) What is the purpose of S-boxes in DES? Explain the avalanche effect
- S-box is used for substitution of bits.
- There are 8 S-boxes in DES
- S-box takes 6 bits as input in which first and last bit represent row number
- Middle 4 bits show the column number
Avalanche effect:
The avalanche effect ensures that even a single-bit change in the plaintext or the key causes a substantial change in the ciphertext.
This property is crucial for ensuring the security of the cipher against various attacks, as it makes it computationally infeasible for attackers to predict the output or recover the plaintext from the ciphertext without knowledge of the key.
(b) What is cryptographic checksum or message authentication code Describe the three situations in which message authentication code is used
A cryptographic checksum, also known as a Message Authentication Code (MAC), is a cryptographic construct used to verify the integrity and authenticity of a message or data transmission.
It is generated using a cryptographic algorithm and a secret key, allowing the receiver to verify that the message has not been tampered with and was indeed sent by the purported sender.
The situations in which they are used:
- Message Integrity Verification:
- One of the primary uses of a Message Authentication Code is to ensure the integrity of a message during transmission. By appending a MAC to a message, the sender can ensure that the recipient can verify that the message has not been altered during transit. Any modifications made to the message, intentionally or unintentionally, will result in a mismatch between the computed MAC and the received MAC, indicating tampering.
- Message Authenticity:
- MACs also provide a means to authenticate the sender of a message. Since the MAC is generated using a secret key known only to the sender and the recipient, the recipient can verify that the message was indeed sent by the purported sender. This prevents unauthorized parties from impersonating the sender and sending fraudulent messages.
- Secure Communication Protocols:
- Message Authentication Codes are commonly used in secure communication protocols to ensure the integrity and authenticity of transmitted data. For example, in network protocols like TLS (Transport Layer Security) and IPSec (Internet Protocol Security), MACs are used to protect the integrity of data exchanged between communicating parties. Similarly, in file transfer protocols like SFTP (SSH File Transfer Protocol) and AS2 (Applicability Statement 2), MACs are used to verify the integrity of transferred files.
(c) Discuss RSA algorithm. Also Find d and cipher text C using P=3 q=11 e=7 and m=10
RSA Algorithm:
RSA (Rivest-Shamir-Adleman) is an asymmetric encryption algorithm used for secure communication and digital signatures.
Steps in RSA:
- Take two prime numbers p and q.
- Find the value of n which is defined as n = p * q
Find the value of Euler’s pie
θ(n) = θ(p) * θ(q)
= (p-1) * (q-1)
Find the value of public key e, which follows below property -
gcd(e, θ(n)) = 1
Find the value of private key using formula
ed mod θ(n) = 1
- To convert plain text to cipher text, formula is
- To convert cipher text to plain text, use
Given,
p = 3, q = 11, e = 7, m = 10
θ(n) = (p-1)(q-1) = 2 10 = 20
d =
=
=
= 21 / 7 = 3
d = 3
Cipher text -
c =
=
=
= (10 1 1) mod 33
= 10 mod 33
= 10
OR
Q4
Q5
OR
Q5
(a) Explain Arbitrated Digital signature
Digital signature is used for authentication of the user.
There are two types of digital signature -
- Arbitrated digital signature
- Direct digital signature
Arbitrated digital signature is a cryptographic protocol where a trusted third party, known as the arbitrator, is involved in the signing process. In this protocol:
- Signing Process: The message sender (signer) generates a digital signature for the message using their private key.
- Arbitration: Instead of directly sending the signature to the recipient, the signer sends the signature along with the message to the arbitrator.
- Verification: The arbitrator receives the message and the signature. It verifies the signature's validity by decrypting it with the signer's public key.
- Confirmation: If the signature is valid, the arbitrator sends a confirmation to the recipient along with the message and signature.
- Recipient Verification: The recipient verifies the confirmation received from the arbitrator to ensure that the message was indeed signed by the sender and is unaltered.
(b) Write the key distribution scenario in which each user shares a unique
master key with key distribution center.

Key distribution center (KDC):
- Key distribution center distributes key to authenticate sender and receiver
- Registration: Each user is registered with the key distribution center. During registration, the user generates a unique master key (or password) known only to them.
- Master Key Exchange: The user securely shares their master key with the key distribution center. This exchange can occur through secure channels such as encrypted communication or physical delivery.
- Master Key Storage: The key distribution center securely stores the master keys of all registered users in its database. The master keys are encrypted or hashed to protect them from unauthorized access.
- Key Distribution: When two users need to communicate securely, they request session keys from the key distribution center for their communication session.
- Session Key Generation: The key distribution center generates a unique session key for each user pair using their respective master keys. This session key is used for encrypting and decrypting the communication between the users.
- Session Key Distribution: The key distribution center securely distributes the session keys to the communicating users. This distribution can occur through encrypted communication channels or using secure protocols.
- Communication: The users can now communicate securely using the session key provided by the key distribution center. The session key is used for encrypting and decrypting the messages exchanged between the users.
- Session Key Expiration: After the communication session is completed, the session key is no longer needed. It can be securely discarded, and the users can request new session keys from the key distribution center for future communication sessions.
(c) Write a note on Secure Socket Layer
- Secure Socket Layer (SSL) is a cryptographic protocol designed to provide secure communication over the Internet.
- It ensures that data transmitted between a client and a server is encrypted and remains confidential
Architecture:
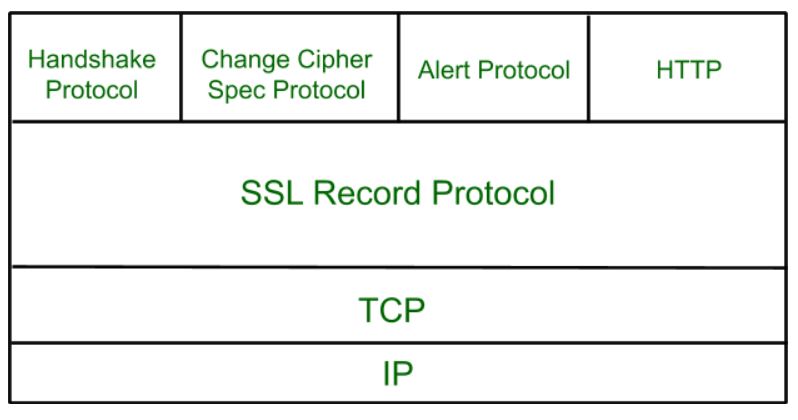
- Hand-shake protocol
- It is used for secure TCP connection between client and server which provides authentication
- Change Cipher protocol
- It is used to store one data of one bit whose value is 1.
- Alert protocol
- This protocol is used to convey SSL-related alerts to the peer entity. Each message in this protocol contains 2 bytes.
- HTTP
- It is used for communication between client and server,
- SSL Record protocol
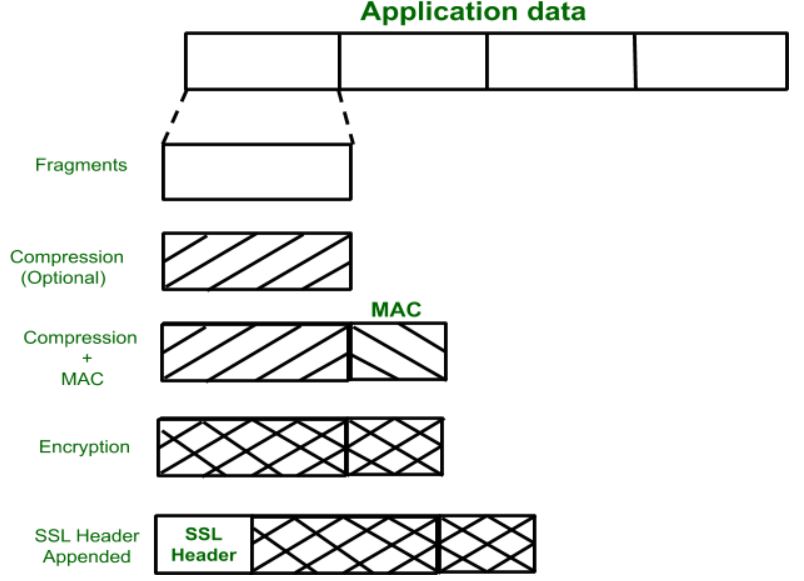
First, data is divided into fragments. After which the fragment is compressed and then encrypted MAC (Message Authentication Code) generated by algorithms like SHA (Secure Hash Protocol) and MD5 (Message Digest) is appended.
Handshake Protocol:
Handshake Protocol is used to establish sessions. This protocol allows the client and server to authenticate each other by sending a series of messages to each other.
